SPYRUS, Inc., headquartered in San Jose, California, develops, manufactures, and markets hardware-based encryption, authentication, and digital content security products. SPYRUS’s products provide a high level of security for the US government, industries that have to meet strict security regulations and simple users that want the best protection for their personal information. SPYRUS implement the strongest cryptographic algorithms commercially available, designed to exceed the highest standards of security certification.
Secure remote access
Encourage remote access with secure and user-friendly solutions
Today, most enterprises offer employees the option to work from home in some way or another. However, attacks on endpoints are increasing and organizations are gaining awareness of the security issues that come with remote access.
Often, there is no budget to buy new PCs for teleworkers and thus employees use their personal computers as the primary tool for their work and network access. This causes great strain to the company’s help desk as employees run and install different applications including malware and viruses.
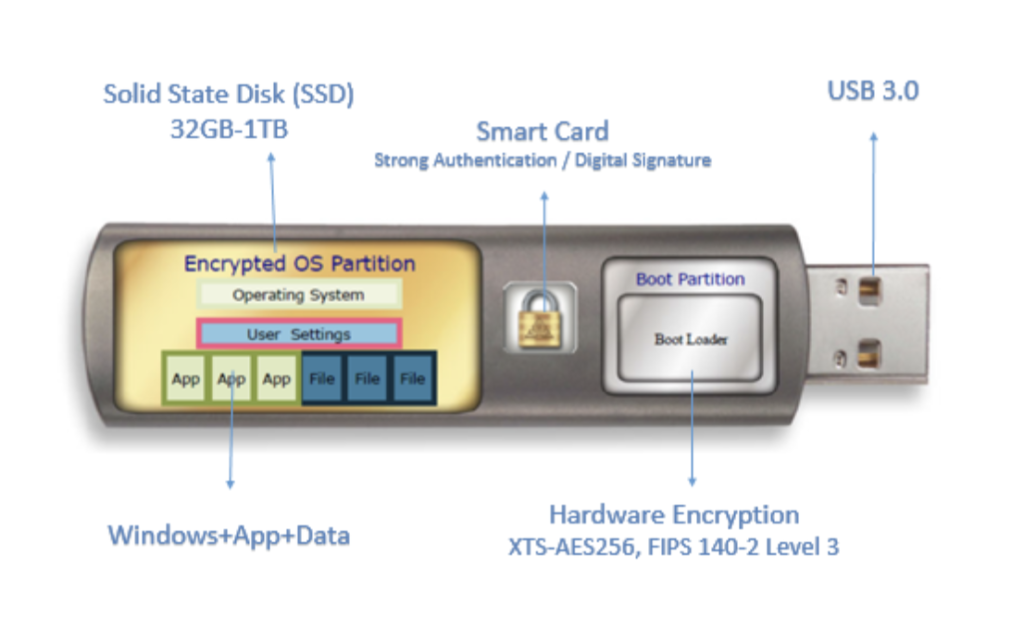
Windows To Go Live Drives allows organizations full control over their remote end-points, including the operating system, the latest Anti-Virus and VPN Client, thus guaranteeing secure remote access for their employees. The Windows To Go Live Drive device leaves no trace on the host PC.
Advantages:
Secure / protected and encrypted hardware device.
Full Enterprise Desktop which allows better user experience than VDI and working offline.
Allows BYOD office (including Mac).
Simple remote operational connectivity (Plug & Play).
Save up to 70% compared to Laptops and save on operating costs.
Solution for confidential information mobility.
Employees “travel light” with our Windows To Go Live Drives that fit right in your pocket.
Please fill out this form: